Yogasawah is proudly powered by Blogger.
Designed by Nyolong Dari Didats Triadi
Counter Strike v1.6 [Portable]
 Monday, August 28, 2006
Monday, August 28, 2006  Add a comment
Add a comment
VA Utilities [Portable]
 Sunday, August 27, 2006
Sunday, August 27, 2006  Add a comment
Add a comment
Portable Bandwidth Monitor 2.9.623
Portable FlashFXP 3.2.0.1080 SE
Portable Limewire 4.12.3 Pro
Portable WinRar 3.5
Portable Winamp 5.21 Pro
Portable Skype 2.5.0.113fr
Portable Dreamweaver 8
Portable QuarkXPress 7.0 Multi
Portable aMSN 0.95 Multi
Portable Easy DVDCD Burner 3.0.76
Portable K-Meleon Browser 1.0
Portable O&O FormatRecovery 4.0 build 719
Portable VCDCutter Pro 4.1.13
Portable Active File Recovery Software 7.1
Portable Firefox 1.5.0.4 + Extensions
Portable WinHKI v1.68 Pro
Portable FlashFXP 3.2.0.1080 SE
Portable Limewire 4.12.3 Pro
Portable WinRar 3.5
Portable Winamp 5.21 Pro
Portable Skype 2.5.0.113fr
Portable Dreamweaver 8
Portable QuarkXPress 7.0 Multi
Portable aMSN 0.95 Multi
Portable Easy DVDCD Burner 3.0.76
Portable K-Meleon Browser 1.0
Portable O&O FormatRecovery 4.0 build 719
Portable VCDCutter Pro 4.1.13
Portable Active File Recovery Software 7.1
Portable Firefox 1.5.0.4 + Extensions
Portable WinHKI v1.68 Pro
Data Recovery

 Add a comment
Add a comment
Power Data Recovery v2.1.0
One of the most powerful data recovery software.
Power Data Recovery is a risk-free and READ ONLY data recovery utility that helps you in recovering your all important data lost after accidental format, virus problems, software malfunction, file/directory deletion, or even a sabotage! It is an easy to use data recovery utility that examines your inaccessible hard drives for damages and corruptions and recovers the data back.
Recovery Ability
Solution
Recover deleted files even if emptied from the Recycle Bin.
Recover formatted partition.
Recover your files after a hard disk crash.
Get data back after a partitioning error.
Recover from hard drive, camera card, USB, Zip, floppy disk or other media.
Key Features
* Supported file systems: FAT 12/16/32 (used by hard disks, disks, Smartmedia™, Compact Flash™, Memory Stick and other) and NTFS (used by hard drives)
* Easy to use and 4 steps to recover your lost data. No technical knowledge needed.
* Ability to scan all volumes in a local machine and build a directory tree of all lost and deleted files.
* Saving data to any windows (including network drives, removable media, etc.) drive possible.
* Supports NTFS compressed and encrypted files.
* Supported Dynamic Volume: Simple Volume, Spanned Volume, Stripe Volume, Mirror Volume,Raid-5 Volume.
* Ability to resume the last recovery result.
File System Supported
* FAT12, FAT16, FAT32, VFAT, NTFS and NTFS5 File system.
System Requirements
* 486 or Pentium-class processor IDE/SATA/SCSI hard drive 64MB RAM (128 MB recommended) Windows 98/Me/NT/2000/XP/2003, 100 MB of free space. Second hard disk is recommended for recovery.
Installation instructions:
Copy the file`s "key.dat" and "krack.exe" to the install
folder and apply, once you have installed the software itself!!
One of the most powerful data recovery software.
Power Data Recovery is a risk-free and READ ONLY data recovery utility that helps you in recovering your all important data lost after accidental format, virus problems, software malfunction, file/directory deletion, or even a sabotage! It is an easy to use data recovery utility that examines your inaccessible hard drives for damages and corruptions and recovers the data back.
Recovery Ability
Solution
Recover deleted files even if emptied from the Recycle Bin.
Recover formatted partition.
Recover your files after a hard disk crash.
Get data back after a partitioning error.
Recover from hard drive, camera card, USB, Zip, floppy disk or other media.
Key Features
* Supported file systems: FAT 12/16/32 (used by hard disks, disks, Smartmedia™, Compact Flash™, Memory Stick and other) and NTFS (used by hard drives)
* Easy to use and 4 steps to recover your lost data. No technical knowledge needed.
* Ability to scan all volumes in a local machine and build a directory tree of all lost and deleted files.
* Saving data to any windows (including network drives, removable media, etc.) drive possible.
* Supports NTFS compressed and encrypted files.
* Supported Dynamic Volume: Simple Volume, Spanned Volume, Stripe Volume, Mirror Volume,Raid-5 Volume.
* Ability to resume the last recovery result.
File System Supported
* FAT12, FAT16, FAT32, VFAT, NTFS and NTFS5 File system.
System Requirements
* 486 or Pentium-class processor IDE/SATA/SCSI hard drive 64MB RAM (128 MB recommended) Windows 98/Me/NT/2000/XP/2003, 100 MB of free space. Second hard disk is recommended for recovery.
Installation instructions:
Copy the file`s "key.dat" and "krack.exe" to the install
folder and apply, once you have installed the software itself!!
Download : Rapidshare
GetBackData Versi Portable
Download : Rapidshare
Tool buat Ngebom LAN

 Add a comment
Add a comment
WinArpAttacker 3.50 Readme
Jun. 4th 2006
Author : unshadow
-----------------------------------------------------------------------------
Contents
1. Overview
2. System Requirement
3. What's New
4. Getting Started
5. Known Issues
6. Revision History
7. To do
-----------------------------------------------------------------------------
1. Overview
------------------------------------
WinArpAttacker is a program that can scan,attack,detect and protect computers on local area network.
The features as following:
1.1 Scan
-. It can scan and show the active hosts on the LAN within a very short time (~2-3 seconds).
It has two scan mode, one is normal scanning, the other is antisniff scanning. The later is to find who is sniffing on the lan.
-. It can save and load computer list file.
-. It can scan the Lan regularly for new computer list.
-. It can update the computer list in passive mode using sniffing technology, that is, it can update the computer list from the sender's address of arp request packets without scanning the lan.
-. It can perform advanced scanning when you open advanced scanning dialg on menu.
-. It can scan a B class ip range in advanced scan dialg.
-. It can scan acthost listed in event listview.
1.2 Attack
-. It can pull and collect all the packets on the LAN.
-. It can perform six attacking actions as following:
(1) Arp Flood - Send ip conflict packets to target computers as fast as possible, if you send too much, the target computers will down. :-(
(2) BanGateway - Tell the gateway a wrong mac address of target computers, so the targets can't receive packet from the internet. This attack is to forbid the targets access the internet.
(3) IPConflict - Like Arp Flood, send ip conflict packets to target computers regularly, maybe the users can't work because of regular ip conflict message. what's more, the targets can't access the lan.
(4) SniffGateway - Spoof the targets and the gateway, you can use sniffer to collect packets between them.
(5) SniffHosts - Spoof among two or above targets, you can use sniffer to collect packets among all of them. (dangerous!!!!)
(6) SniffLan - Just like SniffGateway, the difference is that SniffLan sends broadcast arp packets to tell all computers on the lan that this host is just the gateway, So you can sniff all the data between all hosts with the gateway.(dangerous!!!!!!!!!!!!!!)
-. While spoofing ARP tables, it can act as another gateway (or ip-forwarder) without other users' recognition on the LAN.
-. It can collect and forward packets through WinArpAttacker's ipforward function, you had best check disable system ipforward function because WinArpAttacker can do well.
-. All data sniffed by spoofing and forwarded by WinArpAttacker ipforward function will be counted, as you can see on main interface.
-. As your wish, the arp table is recovered automatically in a little time (about 5 seconds). Your also can select not to recover.
1.3 Detect
-. What is the most important function, it can detect almost all attacking actions metioned as above as well as host status. the event WinArpAttacker can detect is listed as following:
SrcMac_Mismath - Host sent an arp packet, its src_mac doesn't match,so the packet will be ignored.
DstMac_Mismath - Host recv an arp packet, its dst_mac doesn't match,so the packet will be ignored.
Arp_Scan - Host is scanning the lan by arp request for a hosts list.
Arp_Antisniff_Scan - Host is scanning the lan for sniffing host,thus the scanner can know who is sniffing.
Host_Online - Host is online now.
Host_Modify_IP - Host modified its ip to or added a new IP.
Host_Modify_MAC - Host modified its mac address.
New_Host - New gost was found.
Host_Add_IP - Host added a new ip address.
Multi_IP_Host - Host has multi-ip addresses.
Multi_Mac_Host - Host has multi-mac addresses.
Attack_Flood - Host sends a lot of arp packets to another host ,so the target computer maybe slow down.
Attack_Spoof - Host sends special arp packets to sniff the data two targets , so the victims' data exposed.
Attack_Spoof_Lan - Host lets all host on the lan believe that it's just a gateway, so the intruder can sniff all hosts' data to the real gateway.
Attack_Spoof_Ban_Access - Host told host that host has a inexist mac,so the targets can't communicate with each other.
Attack_Spoof_Ban_Access_GW - Host told host that the gateway has a inexist mac, so the target can't access the internet through the gateway.
Attack_Spoof_Ban_Access_Lan - Host broadcast host's mac as a inexist mac, so the target can't communicate with all hosts on the lan.
Attack_IP_Conflict - Host found another host has same ip as its, so the target would be disturbed by ip conflict messages.
Local_Arp_Entry_Change - now WinArpAttacker can watch local arp entry, when a host's mac address in local arp table is changed, WinArpAttacker can report.
Local_Arp_Entry_Add - When a mac address of a host is added to local arp table, WinArpAttacker can report.
-. It can explain each event which WinArpAttacker detected.
-. It can save events to file.
1.4 Protect
-. Support arp table protect. when WinArpAttacker detects local or remote host's is being arp-spoofing, it will recover local or remote host's arp tables as you wish.
1.5 Proxy Arp
-. When hosts on your lan request other hosts' mac address, WinArpAttacker will tell it a certain mac address as you wish.
-. It aims to realize accessing the internet without changing your ip on a new lan, but it also can make your lan in a big mass if you assign a wrong mac address.
1.6 Save arp packets
-. It can save all sniffed arp packets to file.
1.7 other features.
-. Support multi-network adapter and multi-ip address and multi-gateway on a computer, you can select different adapter and ip address to scan different lan.
-. Support DHCP and fixed ip address.
-. Count all the arp packets for each host, including sent and recieved arp packets.
Arp R/S Q/P
| |
Action(Recive/Send) Arp packets type(ReQuest/RePly)
- - - -
ArpRQ meaning: The number of arp request packets recieved
ArpRP meaning: The number of arp reply packets recieved
ArpSQ meaning: The number or arp request packets sent
ArpSP meaning: The number or arp reply packets sent
2. System Requirement.
------------------------------------
-. Local : Windows XP/2000/2003(But I hadn't tested it under Windows XP/2003)
-. Remote : All computers including network devices
-. WinPcap driver 3.1/lastest must be needed.
3. What's New
------------------------------------
+ It can scan a large ip range for online hosts by advanced scanning mode.
+ It can protect local and reomte hosts from arp-spoofing.
+ It can enable proxy arp, act as a arp proxy.
+ It can save all sniffed arp packets to file.
4. Getting Started
------------------------------------
-. Firtly, install the latest WinPcap driver.
-. second, just run WinArpAttacker.exe
-. click scan button and start button
-. look at arp information on remote computer with "arp -a"
-. to stop attack, click stop button.
-. to select adapter or ip address, click options button.
-. to modify attacking setup, click options button.
5. Known Issues
1) This program should be run with administrator privilege.
If not, the program will work abnormally.
2) The attacking action is dangerous, so you must be caution.
3) If there are many active hosts (more than 50) and the real gateway may be down on LAN.
6. Revision History
------------------------------------
= bug fixed
+ improvement/modification
[Start of Versions History]
Version 3.50 ( Jun. 4,2006)
+ It can detect local arp table's change.
+ It can protect local and reomte hosts from arp-spoofing.
+ It can enable proxy arp, act as a arp proxy.
+ It can save all sniffed arp packets to file.
+ It allows you send arp packets manunally.
Version 3.02 ( Apr. 26,2006)
+ It can scan a large ip range for online hosts by advanced scanning mode.
Version 3.00 ( Oct. 07, 2005)
--------------------------------
+ It can detect attacking actions.
+ Add serval scanning mode.
+ It can update the host list from ip packets.
Version 1.50 ( May. 16, 2005)
--------------------------------
+ It can scan the Lan regularly for new computer list.
+ It can update the computer list in passive mode using sniffing technology, that is, it can update the computer list from the sender's address of arp request packets without scanning the lan.
+ Add two options: auto scan and update in passive mode.
+ It can diplay localhost's ip address , mac address, gateway ip address and current computer list status on status bar.
+ Add taskbar icon support, if you close the WinArpAttacker's window, it will leave a icon on taskbar, not really close, thus it can update computer list on the background.
Version 1.10 ( April. 27, 2005)
--------------------------------
+ Support DHCP and fixed ip address.
= When flood attack started, to click stop can't really stop flood attacking.
= IP address is incorrectly sorted when 10.1.0.1 and 192.168.1.1 coexists.
= When PacketSendPacket failed, to exit program will encounter an invalid operator.
Version 1.00 ( April. 16, 2005)
--------------------------------
This program is released.
[End of Versions History]
7. To do
Jun. 4th 2006
Author : unshadow
-----------------------------------------------------------------------------
Contents
1. Overview
2. System Requirement
3. What's New
4. Getting Started
5. Known Issues
6. Revision History
7. To do
-----------------------------------------------------------------------------
1. Overview
------------------------------------
WinArpAttacker is a program that can scan,attack,detect and protect computers on local area network.
The features as following:
1.1 Scan
-. It can scan and show the active hosts on the LAN within a very short time (~2-3 seconds).
It has two scan mode, one is normal scanning, the other is antisniff scanning. The later is to find who is sniffing on the lan.
-. It can save and load computer list file.
-. It can scan the Lan regularly for new computer list.
-. It can update the computer list in passive mode using sniffing technology, that is, it can update the computer list from the sender's address of arp request packets without scanning the lan.
-. It can perform advanced scanning when you open advanced scanning dialg on menu.
-. It can scan a B class ip range in advanced scan dialg.
-. It can scan acthost listed in event listview.
1.2 Attack
-. It can pull and collect all the packets on the LAN.
-. It can perform six attacking actions as following:
(1) Arp Flood - Send ip conflict packets to target computers as fast as possible, if you send too much, the target computers will down. :-(
(2) BanGateway - Tell the gateway a wrong mac address of target computers, so the targets can't receive packet from the internet. This attack is to forbid the targets access the internet.
(3) IPConflict - Like Arp Flood, send ip conflict packets to target computers regularly, maybe the users can't work because of regular ip conflict message. what's more, the targets can't access the lan.
(4) SniffGateway - Spoof the targets and the gateway, you can use sniffer to collect packets between them.
(5) SniffHosts - Spoof among two or above targets, you can use sniffer to collect packets among all of them. (dangerous!!!!)
(6) SniffLan - Just like SniffGateway, the difference is that SniffLan sends broadcast arp packets to tell all computers on the lan that this host is just the gateway, So you can sniff all the data between all hosts with the gateway.(dangerous!!!!!!!!!!!!!!)
-. While spoofing ARP tables, it can act as another gateway (or ip-forwarder) without other users' recognition on the LAN.
-. It can collect and forward packets through WinArpAttacker's ipforward function, you had best check disable system ipforward function because WinArpAttacker can do well.
-. All data sniffed by spoofing and forwarded by WinArpAttacker ipforward function will be counted, as you can see on main interface.
-. As your wish, the arp table is recovered automatically in a little time (about 5 seconds). Your also can select not to recover.
1.3 Detect
-. What is the most important function, it can detect almost all attacking actions metioned as above as well as host status. the event WinArpAttacker can detect is listed as following:
SrcMac_Mismath - Host sent an arp packet, its src_mac doesn't match,so the packet will be ignored.
DstMac_Mismath - Host recv an arp packet, its dst_mac doesn't match,so the packet will be ignored.
Arp_Scan - Host is scanning the lan by arp request for a hosts list.
Arp_Antisniff_Scan - Host is scanning the lan for sniffing host,thus the scanner can know who is sniffing.
Host_Online - Host is online now.
Host_Modify_IP - Host modified its ip to or added a new IP.
Host_Modify_MAC - Host modified its mac address.
New_Host - New gost was found.
Host_Add_IP - Host added a new ip address.
Multi_IP_Host - Host has multi-ip addresses.
Multi_Mac_Host - Host has multi-mac addresses.
Attack_Flood - Host sends a lot of arp packets to another host ,so the target computer maybe slow down.
Attack_Spoof - Host sends special arp packets to sniff the data two targets , so the victims' data exposed.
Attack_Spoof_Lan - Host lets all host on the lan believe that it's just a gateway, so the intruder can sniff all hosts' data to the real gateway.
Attack_Spoof_Ban_Access - Host told host that host has a inexist mac,so the targets can't communicate with each other.
Attack_Spoof_Ban_Access_GW - Host told host that the gateway has a inexist mac, so the target can't access the internet through the gateway.
Attack_Spoof_Ban_Access_Lan - Host broadcast host's mac as a inexist mac, so the target can't communicate with all hosts on the lan.
Attack_IP_Conflict - Host found another host has same ip as its, so the target would be disturbed by ip conflict messages.
Local_Arp_Entry_Change - now WinArpAttacker can watch local arp entry, when a host's mac address in local arp table is changed, WinArpAttacker can report.
Local_Arp_Entry_Add - When a mac address of a host is added to local arp table, WinArpAttacker can report.
-. It can explain each event which WinArpAttacker detected.
-. It can save events to file.
1.4 Protect
-. Support arp table protect. when WinArpAttacker detects local or remote host's is being arp-spoofing, it will recover local or remote host's arp tables as you wish.
1.5 Proxy Arp
-. When hosts on your lan request other hosts' mac address, WinArpAttacker will tell it a certain mac address as you wish.
-. It aims to realize accessing the internet without changing your ip on a new lan, but it also can make your lan in a big mass if you assign a wrong mac address.
1.6 Save arp packets
-. It can save all sniffed arp packets to file.
1.7 other features.
-. Support multi-network adapter and multi-ip address and multi-gateway on a computer, you can select different adapter and ip address to scan different lan.
-. Support DHCP and fixed ip address.
-. Count all the arp packets for each host, including sent and recieved arp packets.
Arp R/S Q/P
| |
Action(Recive/Send) Arp packets type(ReQuest/RePly)
- - - -
ArpRQ meaning: The number of arp request packets recieved
ArpRP meaning: The number of arp reply packets recieved
ArpSQ meaning: The number or arp request packets sent
ArpSP meaning: The number or arp reply packets sent
2. System Requirement.
------------------------------------
-. Local : Windows XP/2000/2003(But I hadn't tested it under Windows XP/2003)
-. Remote : All computers including network devices
-. WinPcap driver 3.1/lastest must be needed.
3. What's New
------------------------------------
+ It can scan a large ip range for online hosts by advanced scanning mode.
+ It can protect local and reomte hosts from arp-spoofing.
+ It can enable proxy arp, act as a arp proxy.
+ It can save all sniffed arp packets to file.
4. Getting Started
------------------------------------
-. Firtly, install the latest WinPcap driver.
-. second, just run WinArpAttacker.exe
-. click scan button and start button
-. look at arp information on remote computer with "arp -a"
-. to stop attack, click stop button.
-. to select adapter or ip address, click options button.
-. to modify attacking setup, click options button.
5. Known Issues
1) This program should be run with administrator privilege.
If not, the program will work abnormally.
2) The attacking action is dangerous, so you must be caution.
3) If there are many active hosts (more than 50) and the real gateway may be down on LAN.
6. Revision History
------------------------------------
= bug fixed
+ improvement/modification
[Start of Versions History]
Version 3.50 ( Jun. 4,2006)
+ It can detect local arp table's change.
+ It can protect local and reomte hosts from arp-spoofing.
+ It can enable proxy arp, act as a arp proxy.
+ It can save all sniffed arp packets to file.
+ It allows you send arp packets manunally.
Version 3.02 ( Apr. 26,2006)
+ It can scan a large ip range for online hosts by advanced scanning mode.
Version 3.00 ( Oct. 07, 2005)
--------------------------------
+ It can detect attacking actions.
+ Add serval scanning mode.
+ It can update the host list from ip packets.
Version 1.50 ( May. 16, 2005)
--------------------------------
+ It can scan the Lan regularly for new computer list.
+ It can update the computer list in passive mode using sniffing technology, that is, it can update the computer list from the sender's address of arp request packets without scanning the lan.
+ Add two options: auto scan and update in passive mode.
+ It can diplay localhost's ip address , mac address, gateway ip address and current computer list status on status bar.
+ Add taskbar icon support, if you close the WinArpAttacker's window, it will leave a icon on taskbar, not really close, thus it can update computer list on the background.
Version 1.10 ( April. 27, 2005)
--------------------------------
+ Support DHCP and fixed ip address.
= When flood attack started, to click stop can't really stop flood attacking.
= IP address is incorrectly sorted when 10.1.0.1 and 192.168.1.1 coexists.
= When PacketSendPacket failed, to exit program will encounter an invalid operator.
Version 1.00 ( April. 16, 2005)
--------------------------------
This program is released.
[End of Versions History]
7. To do
Download : WinArpAttacker
-----------------------------------------------------------------------------
WinArpAttacker is based on wpcap, you must install wpcap driver before running it.
wpcap
If you had installed old version of winpcap, just install WinPcap_3_1.exe overwrite it.
-----------------------------------------------------------------------------
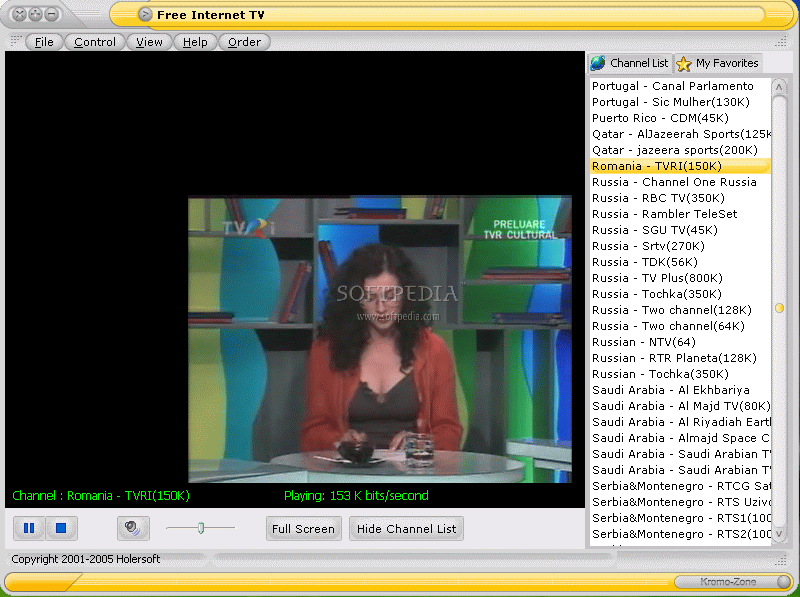
Free Internet TV 700 Channel
 Wednesday, August 23, 2006
Wednesday, August 23, 2006  Add a comment
Add a comment
SoftPerfect Bandwidth Manager 2.5.380

 Add a comment
Add a comment
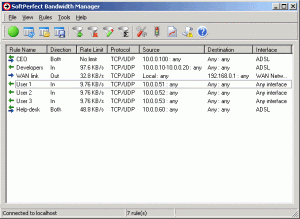
is a full-featured traffic management tool for Windows that offers cost-effective bandwidth control and quality of service based on built-in prioritized rules. These rules can specify a bandwidth limit for each Internet user. With
SoftPerfect Bandwidth Manager, you can apply speed-throttling rules to specified IP addresses, ports and even network interfaces with no changes to existing network infrastructure.
The rich feature set of SoftPerfect Bandwidth Manager is easily managed via the intuitive Windows GUI.
The software requires Windows NT/2000/XP/2003. It also requires a network connection which could be a wireless connection or a modem that conforms to the NDIS standard.
Bandwidth Manager Key features :
Centralized configuration from a single network location.
Flexible, prioritized, bidirectional rules to specify maximum data rates.
Rules for IP addresses, protocols, ports (for TCP/IP) and network interfaces.
Transparency for end users.
No software installation is required on client workstations in most cases.
Detailed and comprehensive statistics are available for each rule.es
Unlimited number of rules
Remote administration
Bridging and address groups
Batch creation of rules
Daily reports
Event log system
Scheduler
Download : Rapidshare
Password : n/a
NetLimiter Pro v.2.08

 Add a comment
Add a comment
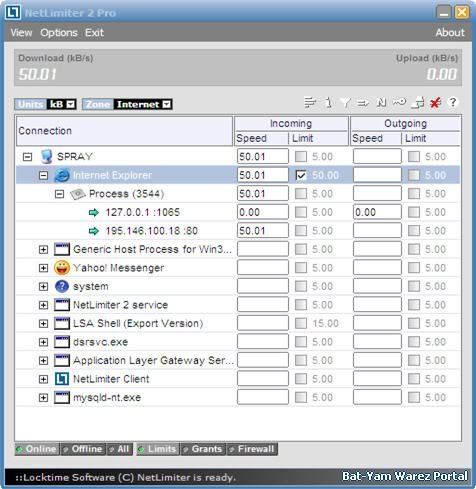
NetLimiter - Ultimate Bandwidth Shaper
NetLimiter is an ultimate internet traffic control and monitoring tool designed for Windows. You can use NetLimiter to set download/upload transfer rate limits for applications or even single connection and monitor their internet traffic.
Along with this unique feature, Netlimiter offers comprehensive set of internet statistical tools. It includes real-time traffic measurement and long-term per-application internet traffic statistics
Main NetLimiter features
-Network Monitor
NetLimiter 2 shows list of all applications communicating over network it's connections, transfer rates and more.
-Bandwidth Limiter / Bandwidth Shaper
You can use NetLimiter 2 to set download or upload transfer rate limits for applications, connections or groups of them. With limits you can easily manage your internet connection?s bandwidth (bandwidth shaper or bandwidth controller)
-Statistical tool
This feature lets you to track your internet traffic history since you've installed NetLimiter 2.
-Additional network information
NetLimiter 2 provides you with and additional information like WHOIS, traceroute etc.
-Rule scheduler (and more...)
Remote administration, Personal firewall, Running as WinNT service, User rights, Chart, Advanced Rule editor and scheduler, Zone based traffic management
Download : Rapidshare
Password : n/a
AgileMessenger

 Add a comment
Add a comment
Buat Yang Demen Chatting via HandPhone. Lumayan murah ber YM ria lewat handphone.
Download : Uploading
Password : n/a
System Tools [Portable]

 Add a comment
Add a comment
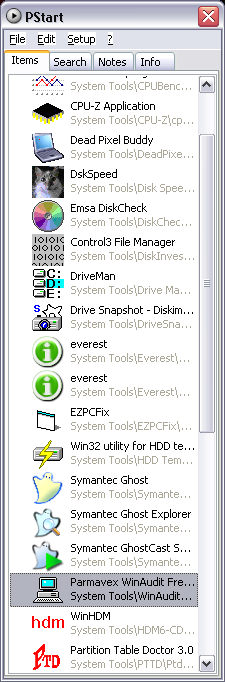
Apps Include:
Aida32
BurnInTest
CPUBench
CPU-Z
DeadPixelBuddy
Disk Speed
DiskCheck
DiskInvestigator
Drive Manager
DriveSnapShot
Everest
EZPCFix
HDD Temperature
HDM6-CD
HDSpeed
MemTest
NeroInfoTool
NeroSpeed
NortonDiskDoctor2005
PowerQuest
PTTD
QuickBench
RAIDReconstructor
RightMarkMA
R-Linux
StorageInfo4Win
SymantecGhost
WinAudit
Download : Rapidshare
Password : n/a
thank's to lord_nara
Multimedia [Portable]

 Add a comment
Add a comment
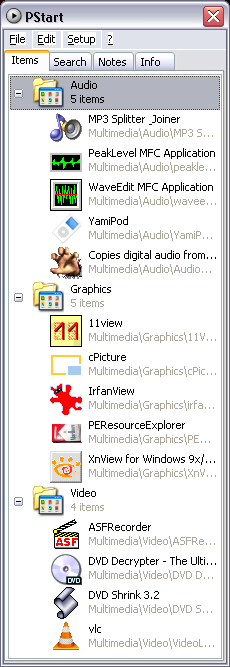
Apps Included:
Audio:
AudioGrabber
MP3 Splitter & Joiner
peaklevel
waveedit
YamiPod
Video:
ASFRecorder
DVD Decrypter
DVD Shrink
VideoLAN
Graphics:
11View
cPicture LE
irfanview
PEResourceExplorer
XnView
Download : Rapidshare
Password : n/a
thank's to lord_nara
Anti Virus [Portable]

 Add a comment
Add a comment

ADAWARE SE
Antivir
AVAST!
McAfee Virus Scan
NOD32
Portable Clam Win
Trend Micro Sys Clean
Download : Rapidshare
Password : n/a
thank's to lord_nara
Burning [Portable]

 Add a comment
Add a comment
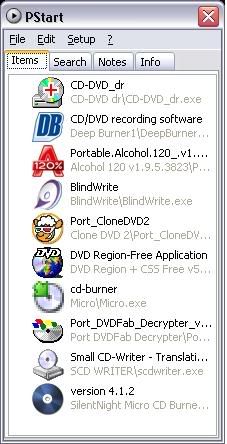
Alcohol 120 v1.9.5.3823
BlindWrite
CD-DVD dr
Clone DVD 2
Deep Burner1
DVD Region + CSS Free v5.9
Micro
Port DVDFab Decrypter
SCD WRITER
SilentNight Micro CD Burner
Download : Rapidshare
Password : n/a
thank's to lord_nara